Apple AirDrop flaw exposes 1.5 billion devices — what to do
Apple tree AirDrop flaw exposes 1.5 billion devices — what to do
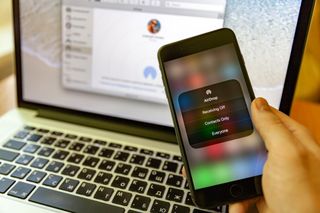
Apple tree's AirDrop protocol can accidentally leak your e-mail address and phone number to whatever Apple device nearby, five German researchers have discovered. They say Apple has known of this problem — which makes 1.5 billion devices vulnerable — for most two years, simply add that they've got a possible solution.
"Information technology is possible to learn the phone numbers and email addresses of AirDrop users -- fifty-fifty equally a complete stranger," states a website put up by the researchers. "An attacker just requires a Wi-Fi-capable device and physical proximity to a target."
- Ransomware gang wants Apple tree to 'buy dorsum' stolen blueprints
- The all-time Mac antivirus software
- Plus: iPhone 13 concept is stunning — and has everything
"Apple users are still vulnerable," the site adds. "They tin only protect themselves past disabling AirDrop discovery in the organisation settings and past refraining from opening the sharing pane."
How to protect yourself
To make sure yous're not vulnerable to these attacks, you'll desire to set your AirDrop to "Receiving Off" on an iPhone or iPad, and to "Allow me to exist discovered by No One" on a Mac.
You might as well want to turn off Wi-Fi and Bluetooth when you're not using them, although it'due south non clear whether doing then will really plow off AirDrop.
Alternatively, you could just let "Everyone" send y'all AirDrop files, because then there won't exist any exchange of electronic mail addresses or phone numbers. You might end up seeing a lot of disturbing images sent past other iPhone users, though.
How AirDrop initiates connections
When your AirDrop-enabled device is prepare to share a file, it broadcasts an encrypted form of your phone number and/or electronic mail address (whichever is tied to your Apple account) to anything within Wi-Fi or Bluetooth range.
It does this so that other Apple devices with AirDrop set to the "Contacts Only" default tin can bank check to come across whether you're in their users' contact lists in case you want to connect. (Devices with AirDrop set up to "Anybody" doesn't perform this check, but notwithstanding receive the encrypted telephone numbers or electronic mail addresses.)
The Apple devices don't circulate actual phone numbers or electronic mail addresses. Rather, they transport out "hashes" of those values, i.e. long strings of text yous get when you run text through fixed mathematical algorithms.
For example, the phone number i (212) 555-1212, with spaces and parentheses removed, would come up out of the SHA-256 hashing algorithm that AirDrop uses as "26321368f6c23510f79a21085024dd5a4f958e6c22dc057a358d1b5a1fc5c932."
Other Apple tree devices check those hashes against the hashes of email addresses and telephone numbers they have in their own contact lists. If a match is made, then those devices reply to yours with their own email and phone-number hashes.
If both devices have each other's contact information in their Contacts listing, so an AirDrop connection is made and files tin can be shared. (Once more, the "Everyone" setting skips this check and only shares files with anyone.)
Sounds good, but there's a trouble
The problem is that while hashes are supposed to be irreversible — you shouldn't be able to punch dorsum a hash to get the original telephone number or electronic mail address — that's not exactly how it works in real life.
"Cryptographic hash functions cannot hide their inputs (chosen preimages) when the input infinite is small or predictable, such every bit for telephone numbers or email addresses," states an academic paper authored by researchers Alexander Heinrich, Matthias Hollick, Thomas Schneider, Milan Stute and Christian Weinert.
Heinrich, Hollick and Stute previously worked on means to attack AirDrop's technical underpinnings.
In other words, considering telephone numbers follow predictable formats, it wouldn't have long for fifty-fifty a midrange calculator to precompile a list of known hashes for all the possible telephone numbers in a specific area code, or all 10 billion or so possible phone numbers in North America.
A hacker could put a precompiled list of telephone-number hashes on his laptop, so sit down in a public place — such as exterior the entrance to a big corporation's headquarters at lunchtime — and passively collect the numbers of nearby iPhones as they try to gear up AirDrop shares.
The hacker could also actively strength other devices to give up their telephone numbers. The assaulter could initiate AirDrop shares by sending out the hash of a telephone number that many people were probable to have in their contact lists — say, a company's main switchboard number, or the number of its human-resources section.
Any passing iPhone with that number in its Contacts listing would transport back the hash of its own phone number.
OK, and so what if a stranger knows my mobile number?
Considering mobile phone numbers are (mistakenly) used every bit identity verification for password challenges, bank-business relationship logins and two-cistron hallmark, yous could cause a lot of damage if yous got the phone numbers of high-contour individuals or anyone who owns a lot of Bitcoin.
Email addresses are a chip harder to precompile hashes for, as they don't adjust to any ready length and tin can incorporate letters as well as numbers. Merely a hacker could limit the precomputed hashes to addresses ending in "@gmail.com" or "@yahoo.com," or to addresses following a company's specific addressing format.
"Alternatively, an attacker could generate an email lookup table from data breaches or apply an online lookup service for hashed e-mail addresses," the paper states.
The hacker could and so harvest email addresses in the aforementioned style every bit the phone numbers. Those email addresses, the research newspaper notes, could be used "for fraudulent activities such as (spear) phishing attacks or making a profit past selling personal data."
A solution presents itself
The Darmstadt researchers said they privately told Apple almost the passive-attack scenario in May 2019, and the active-set on one in Oct 2020. In July 2019, a second group independently found the passive-set on issue and went public with it.
"Apple has not yet commented if they plan to address these AirDrop issues," the research newspaper says. (Tom's Guide has reached out to Apple tree for comment, and we will update this story when we receive a reply.)
The researchers have created an open-source project called "PrivateDrop" that "integrates seamlessly into the electric current AirDrop protocol stack."
They say PrivateDrop, which they told Apple about in October, will ready AirDrop's data-leakage problems by substituting other values for the hashed phone numbers and email addresses.
Source: https://www.tomsguide.com/news/apple-airdrop-flaw-exposes-15-billion-devices-what-to-do
Posted by: gemmillyouser.blogspot.com


0 Response to "Apple AirDrop flaw exposes 1.5 billion devices — what to do"
Post a Comment